Table of Contents
- Introduction
- Server protection solutions
- Recommended solution – Broadcom (Symantec) Integrated Cyber Defense
- Key areas
- Why did we choose this solution over similar solutions?
- Our expertise and certificates
- Endpoint security solutions
- Our recommended solutions - Broadcom (Symantec) Endpoint Protection – Pulse Secure NAC
- How can these solutions be used?
- Broadcom Endpoint Protection
- Pulse Secure Network Access Control – network access control (NAC)
- Why do we recommend these over similar solutions?
- Our expertise and certificates
- Security Information and Event Management (SIEM) solutions
- Broadcom Data Loss Prevention (Symantec DLP)
- Our IT security audit projects
- Inspection plan
- Detection of technical vulnerabilities with software support
- Configuration analysis
- Oral interview
- ISACA exam centre
- Our ISO certifications
Introduction
One of our main areas of activity involves providing training for information security and IT security equipment, as well as related consultancy responsibilities and systems integration and systems monitoring requirements. In the field of information security, we are able to provide various services for our customers with regard to almost any issue, offering ready solutions for the matters of data leakage, log analysis, endpoint protection, virus detection and spam filtering, BCP/DRP plan preparation, IT security audits and Internet security.
Server protection solutions
The protection of IT systems and the data stored in these systems has become a key area of focus in IT security for companies. Even with the use of recommended methodologies and guidelines, it is becoming increasingly difficult to provide adequate protection against coordinated and complex attacks that often involve several continents. Only complex solutions that go beyond what typical security systems offer will be able to protect servers against advanced attacks.
Recommended solution – Broadcom (Symantec) Integrated Cyber Defense
Symantec's integrated cybersecurity platform offers a complex solution for server protection, adding endpoint, web, e-mail and information security, as well as identity protection both for cloud-based and on-premise infrastructures. It is a unique approach in the industry as far as providing the most effective and complete solution.
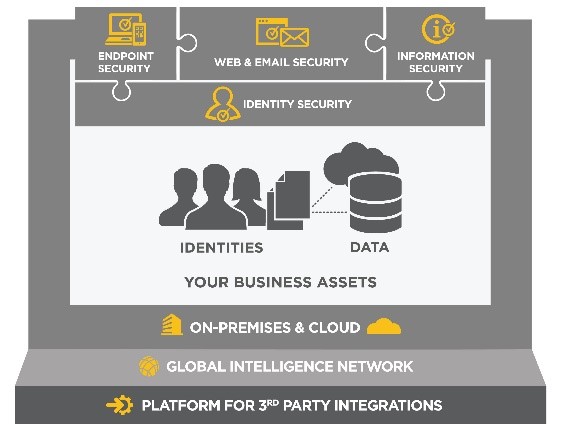
Key areas
Symantec Endpoint Security – The last, critical line of defense for the protection of workstations and servers. Includes effective network and endpoint protection against advanced attacks.
Web and Email Security – E-mail and web services are nowadays essential for every organisation to ensure their day-to-day business operations. Broadcom (formerly Symantec) offers a complete range of web and e-mail security solutions against threats, including isolation and sandbox solutions.
Information Security – Ensures that the company's sensitive data and documents never fall into the wrong hands. Broadcom's security suite, as well as the Data Loss Prevention and Secure Access Cloud products, will offer a suitable solution for the operation of both cloud-based and on-premises infrastructures.
You can find more details below about these areas.
Why did we choose this solution over similar solutions?
This option provides partners with a world-class and industry-leading technology, which many customers in Hungary already use with great satisfaction.
Our expertise and certificates
Our company's portfolio is mainly dominated by IT security solutions, thus our systems engineers have outstanding experience with regard to Broadcom products.
Our systems engineering colleagues have completed the following relevant vendor exams, among others:
- Symantec Endpoint Protection Administrator
- Symantec Messaging Gateway
- Symantec Data Loss Prevention Administrator
- Symantec Certified Trainer
Endpoint security solutions
Due to the ever-evolving and growing enterprise IT toolset, providing endpoint protection is of critical importance nowadays. With the practice of "Bring Your Own Device" (BYOD) becoming common along with the popularity of IoT and other enterprise mobile devices, malicious campaigns targeting endpoints have become increasingly sophisticated and frequent. The implementation of effective security solutions against network threats is now an essential requirement, given the estimate by certain studies that around 70 percent of successful attacks originate from user devices.
Our recommended solutions - Broadcom (Symantec) Endpoint Protection – Pulse Secure NAC
The introduction of multiple layers of protection significantly reduces risks and provides protection for business data. When selecting the appropriate technologies, our company strives to provide comprehensive solutions to ensure secure access to corporate resources.
With regard to endpoint protection systems, we recommend Broadcom Endpoint Protection and Pulse Secure's Network Access Control (NAC) technology as market-leading solutions.
How can these solutions be used?
Broadcom Endpoint Protection
Broadcom's Endpoint Protection product offers the following key functionality to ensure server security:
- comprehensive protection against malware
- advanced machine learning system and file reputation analysis
- intrusion prevention system
- real-time application monitoring
- SONAR technology that identifies malicious threats concerning unknown attacks based on heuristics and algorithms
- protection against known and unknown zero-day attacks
- unified central management system
- optimised support for virtual environments
- support for Linux, Mac and Microsoft operating systems
- notification and reporting capabilities based on security events
- creation of security policies
- remote activation of program components
- option for remote monitoring and remote administration
- network firewall and intrusion protection
- protection against memory exploits
- emulation capabilities
- virus protection
- behaviour analysis
- application and device control
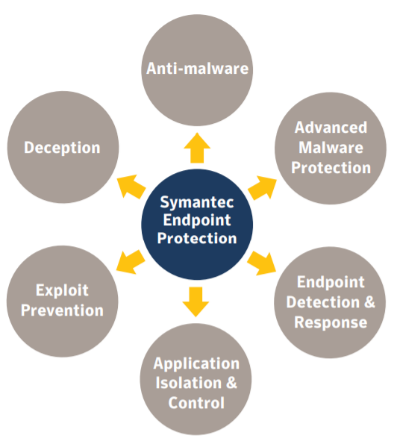
Broadcom's endpoint security system may very well be the right solution both for companies with a few employees and for organisations with thousands of employees, thanks to scalability and resource optimisation. It provides effective protection for devices by means of next-generation technologies. It offers easy integration and thus efficient implementation with other IT infrastructure elements.
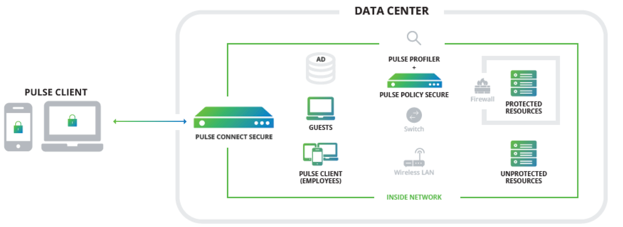
Pulse Secure Network Access Control – network access control (NAC) technology
The network access control solution allows you to control access from user devices to specific organisational resources based on the corporate security policy. The NAC authenticates, maps and profiles each network endpoint and enforces the security policies for the wired or wireless networks.
Key functionalities include the following:
- Pulse Profiler – comprehensive network discovery, monitoring and behaviour analysis
- Pulse Policy Secure – a unified framework for access verification and access control
- Pulse Client – agent and agentless endpoint control, available for multiple platforms
Why do we recommend these over similar solutions?
Both solutions provide partners with a world-class and industry-leading technology, which many Hungarian customers already use with great satisfaction. When picking a solution, our primary objective was to provide truly uncompromised protection.
Our expertise and certificates
Our company's portfolio is mainly dominated by IT security solutions, thus our systems engineers have outstanding experience with regard to installing, configuring, deploying and supporting Broadcom-based solutions as well as Pulse devices. In addition to the completion of numerous training courses, our colleagues are also in possession of Broadcom Endpoint Protection 14 Administrator and Pulse for Enterprise certifications.
Security Information and Event Management (SIEM) solutions
As the use of information technology has become widespread, today's networks are more complicated than ever and protecting them from increasingly complex and sophisticated attacks as well as ensuring continuous IT security may seem a time-consuming, difficult and perhaps a nearly impossible task. The proactive monitoring of systems is essential to ensure the security of assets, equipment, data and business continuity, allowing timely detection and response to potential attacks before they could cause serious damage.
An advanced SIEM solution provides security professionals with greater visibility and centralised management of incidents taking place on the corporate network. The solution additionally assists with the correct prioritisation of incidents that already occurred, so that a response to the most important events and incidents requiring intervention can be executed as quickly as possible.
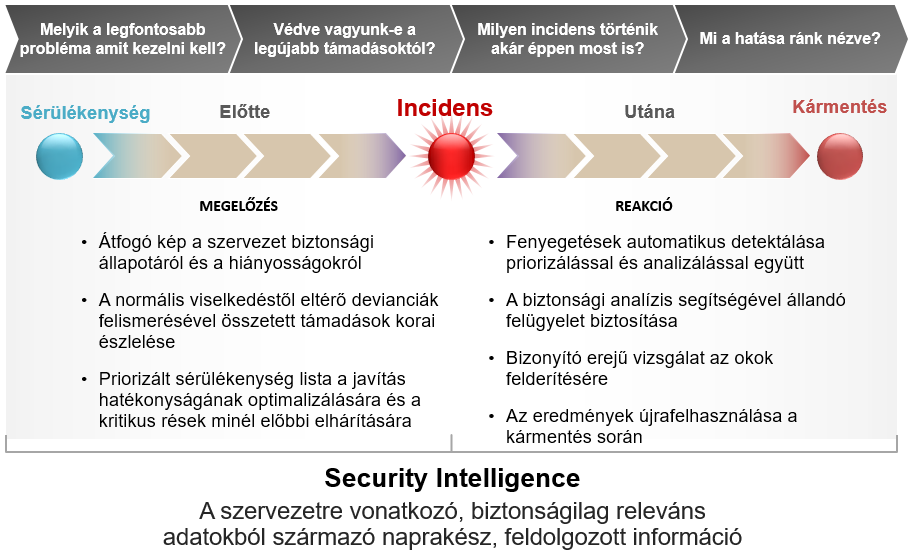
The collection, normalisation (conversion into a standardised format) of security events and the option of automatic incident handling are now considered to be basic requirements for a SIEM system, but different vendors may offer very different solutions with regard to the range of natively supported log sources or the quality of the "underlying intelligence".
IBM Qradar
Our company always takes into account our clients' requirements and strives to provide the most appropriate solution. In most instances, IBM Qradar SIEM (Juniper Secure Analytics) is the best choice in our opinion.
IBM Qradar SIEM has more than 450 log aggregation modules (DSM), which guarantees fast and efficient log aggregation even in the most varied enterprise environments. In case of an unsupported hardware component, custom modules can be easily created, without the need of a developers.
Beyond gathering conventional system logs, IBM Qradar SIEM is capable of receiving and processing traffic logs (Flow) from network equipment. Network attacks can be detected from these logs.
After gathering data, events are prioritized, reports are generated, and correlations are made based on hundreds of correlation rules. There are a number of supplementary software available to further customize the SIEM system.
Broadcom Data Loss Prevention (Symantec DLP)
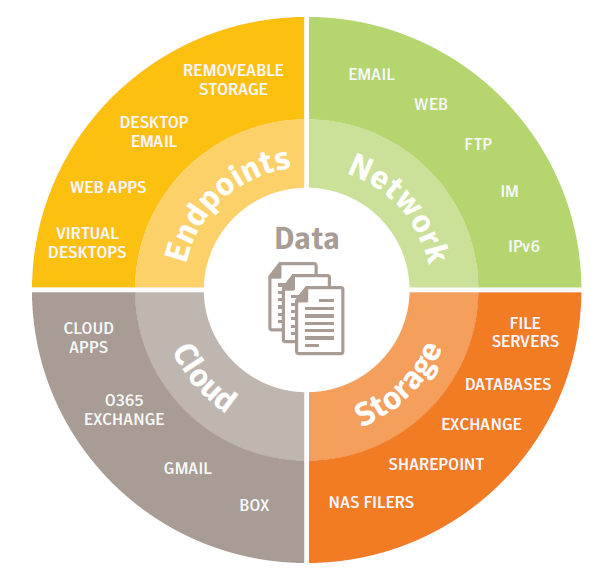
Most companies invest a lot of money and resources into maintaining the physical security of the corporate building and infrastructure elements, but nowadays hardware assets no longer represent the most significant value when it comes to corporate assets. Intellectual property, trade secrets and customer data are all types of information that, if lost, will cause serious financial damage, in addition to loss of company reputation or even market advantage.
Data leakage prevention solutions provide ongoing protection for the company's sensitive data, thereby preventing data leaks, as well as ensuring regulatory compliance and reducing both external and internal threats.
When it comes to currently available data leakage protection solutions, our experts recommend Broadcom's DLP solution, which has been one of the market-leading products for more than 10 years.
Broadcom's data leakage prevention solution offers 4 key features:
- Identification of sensitive corporate data
- Monitoring of the identified data or data that meets certain defined criteria
- Protection of the identified and monitored data
- Execution of the above tasks using a central management interface
With the implemented system in place, it is possible to take an inventory of the company's sensitive data stored in shares or at endpoints in order to track and prevent the transfer of such data from file servers and workstations to the network or even to the cloud. This solution offers the ability to notify the user immediately when data is being accessed or used, thereby also increasing security awareness within the company.
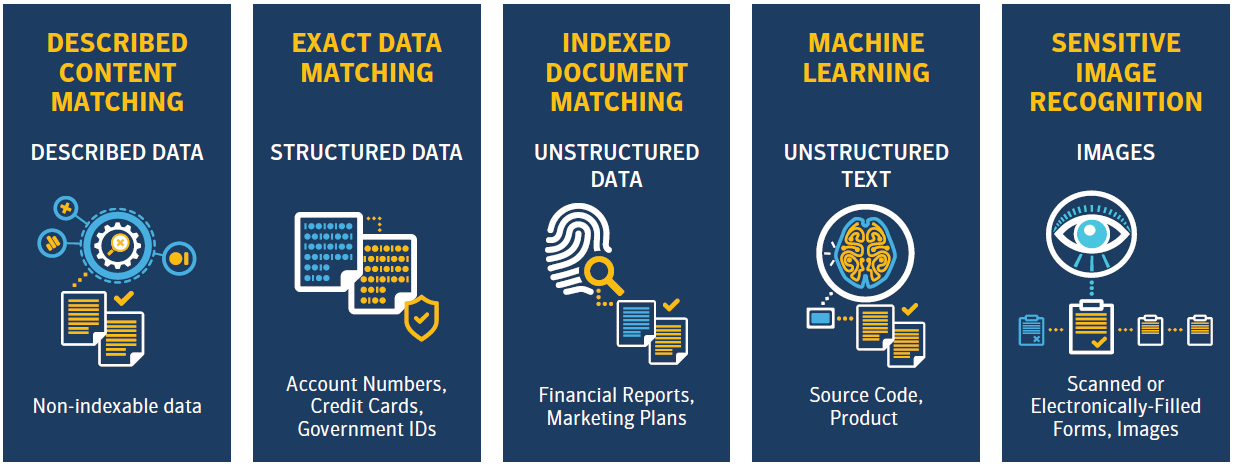
A number of tools are available to detect data movement and leakage, so that in addition to specific descriptive languages, the system can also monitor structured and unstructured data based on an index, or even confidential data placed in images. The system's self-learning capability (VML) allows it to detect even confidential data that is not explicitly included in the rule set.
Beyond the data leakage prevention functionality, additional security is provided by the Symantec Information Centric Security Module, which includes the so-called Information Centric Tagging (ICT) and Information Centric Encryption (ICE) functions.
If you are interested or have further questions about the product, or possibly about your experiences with deployment, we have several certified specialists available (Symantec Certified Specialist (SCS) – Symantec™ Data Loss Prevention 15) with experience in deployment and implementation.
Our IT security audit projects
During our IT audit projects, our company applies the IT audit methodologies of the major international audit firms, the methodology based on the latest version of the ISACA (Information Systems Audit and Control Association) COBIT framework, the MSZ ISO/IEC 27001 and 27002 recommendations, as well as the procedures and methodologies of the national IT security recommendations as previously utilised by our company for several successful projects.
Generally speaking, during our audit projects our aim is also to perform the audit, inspection and correction of all the policies, procedures, practices and organisational structures of each audited system that were designed to provide sufficient assurance that the Customer's business objectives are being met and that undesirable events are being prevented or detected and corrected.
These so-called controls can be divided into three main categories based on the general methodology:
- Organisational controls (activities)
- Management controls (processes)
- Technical controls (procedures)
The above-described grouping of controls as listed above may also be defined according to each individual task, by specifying which ones have
- preventive
- exploratory, or
- corrective
purposes. We perform our general audit projects based on the COBIT methodology, using the COBIT maturity model to define the COBIT maturity level of the organisation in terms of IT governance based on the results of surveys and audits. We also assist our customers in determining the level of development against the general industry standard based on the "best practice" principle that's applicable for the company. Afterwards, we develop a strategic plan based on the current status of the organisation to help achieve the industry standard or a level exceeding the standard.
For our IT security consulting services, we consider and apply the relevant national and international methodologies, recommendations and legal requirements, while also taking into account the current domestic situation and market experiences to evaluate the results.
Generally speaking, the audit task does not cover the complete inspection of the 34 high-level control objectives and the 318 control objectives of COBIT, but instead the general aim is to perform a security audit of the IT systems specified by the Contracting Authority as quickly as possible.
Our methodology concerning systems auditing is tailored to the specific requirements of the Contracting Authorities, so that we generally carry out the following tasks to perform our audit:
- We prepare an audit plan in advance per each defined system, based on the main audit guidelines, which:
- covers the general IT operating environment of the relevant system
- outlines the operations and the operational control environment
- defines the key metrics of the system's operation (such as: number of users, BCP, OCP, DRP relevance).
- Furthermore, we outline the following aspects in relation to the operation of the technical system:
- the main steps of the IT vulnerability assessment process, and
- the main elements of our configuration analyses for the relevant platform.
- In order to audit the security of the processes, we make use of the information collected through the questionnaire provided to us as customized by the client on behalf of the Contracting Authority.
- During the execution of the task, an audit schedule is prepared through cooperation with the customer's project managers, which includes an up-to-date list of the systems to be inspected during the relevant month and the rest of the year.
Inspection plan
For the systems and applications to be investigated, an inspection plan is submitted by us to the Contracting Authority, which includes the resources and schedules in terms of the expectations of the Contracting Authority.
Following the approval of the Contracting Authority, our experts carry out the on-site surveys and inspections. The site (including the option for direct connection to the subnetwork of the system to be inspected, together with the appropriate authorisation) will be provided by the Contracting Authority, and the equipment (laptop, software) necessary to carry out the surveys will be provided by the Tenderer. The Contracting Authority will provide support and access to the site as necessary for the arrangement of the on-site audit. In all cases, the inspection is carried out in the presence and with the support of the computer administrator/system administrator.
The Tenderer guarantees that it is in possession of the licence/right to use the software(s) to be used in the performance of the service for the duration of the project as well as ensures that the inspection is non-destructive and that it does not compromise the operational security and availability of the system/device to be inspected.
The report contains a brief description of the test methodology, the deficiencies found as well as the recommendations for their correction, including a description of the latter.
Detection of technical vulnerabilities with software support
WSH Ltd undertakes the investigation of vulnerabilities in the IT systems specified by the Contracting Authority. We use the latest version of Nessus software for the investigation, and we have the relevant licence for this software.
The hardware environment running the testing software will be provided by us for the entire duration of the investigation. Any vulnerabilities detected by the vulnerability testing software will be further investigated by us, in proportion to the risk they pose with regard to each affected system. We will prepare a detailed report on the detected vulnerabilities and subsequently prepare a recommendation for the removal of these vulnerabilities as well as mitigation of the involved risks, on the basis of the additional information gathered during the configuration analysis and the oral interviews.
The completion of the full vulnerability assessment by the Nessus software requires access to each IT system that the Tenderer will need to authorise.
Configuration analysis
The configuration analysis of the operating systems is carried out based on the ISACA (COBIT) and ISO 27002 guidelines, as well as the vendor recommendations for each operating system. Based on the results of the configuration analysis, we identify the settings that may involve security risks. For the analysis, we use the analysis software available from the vendors of each operating system, where possible (e.g. Microsoft Best Practice Analyzer). As part of the configuration analysis, oral interviews may also be conducted, during which the investigators from WSH Ltd will gather information about the associated server environment to help with exploration of specific errors.
Oral interview
The oral interview includes a check on usage patterns concerning the devices as well as the identification of security risks inherent in user habits. The computer administrator/system administrator on behalf of the Contracting Authority will also be present during the interview. During the oral interviews, we mainly utilise our own questionnaire.
The following topics are always covered during the interviews:
- investigation of operational efficiency,
- examination of the effectiveness of implementation and developments,
- investigation of the change management approach,
- investigation of physical and logical security,
- review of access control,
- review of permissions,
- availability testing.
A detailed transcript of the interviews is drafted, which is later finalised and incorporated into the investigation report after the approval of the interviewee.
ISACA exam centre
Currently, our Exam Center is the exclusive provider of ISACA Centre exams in Hungary. The ISACA Centre developed specialised training courses and a globally accepted certification system concerning the areas of Information Security and Risk Management, Quality Assurance, and Governance. The following ISACA exams covering these areas are available at our exam centre: CISA, CISM, CGEIT, CRISC.
Our ISO certifications
Our integrated quality management system, which complies with the ISO 9001:2000, ISO 14001:1997 and ISO IEC 27001:2014 standards and which covers all WSH activities, is a special guarantee for the reliable performance of the services we undertake to complete.

